Cybersecurity ventures stated that cybercrime is expected to grow by 15% every year. They predicted that those crimes might cost $10.5 trillion annually on a global scale by the year 2025. Security testing plays a vital role in preventing most of these crimes.
In this article, let’s look at five security testing challenges and how to tackle them.
Generally, security requirements are not given equal importance as functional requirements. Sometimes security requirements are considered post-developing certain modules and, in some cases, it is before pre-release. Not defining the security requirements prior makes security testing difficult.
Solution:
Functional test cases are typically given a high level of importance. Even though we write positive and negative cases, it doesn’t have quality test data to cover security use and misuse cases. Sometimes test cases are written before security testing starts. In some cases, security testing is done ad hoc without writing any test cases.
Delaying the test case writing reduces the efficiency and effectiveness of security testing. Since we follow agile methodology, updating the test case based on the new or modified requirements is essential.
Solution:
API security is as important as front-end security. Most of the attacks that happened through security testing at the API level, remained unnoticed unless we were given access to the database. Also, APIs might have some sensitive data exposed to unauthorized users.
APIs are developed early. Therefore, API security testing ensures the basic security requirements are met.
Solution:
This is the biggest challenge. We decided to implement security testing and started self-learning. But there were only a few resources online. Security testing is vast, and we weren’t sure about the proper methods.
Outsourcing might seem a good option but handing the security testing solely to an external team is not preferable. It would be time-consuming, and we might miss some critical security bugs.
An internal team can perform effective preliminary testing as they are aware of the sensitive data to be protected, source code, and requirements.
Solution:
There are various tools available for security testing. The skillset of the tester and the budget determine the selection of tools. Initially, I was using OWASP ZAP. Then I started using Burp Suite on a tech lead’s suggestion.
ZAP is best for API security testing. It is more convenient to get and view all APIs in a site tree using ZAP. Burp Suite is the most preferred tool by most web security testers. Burp Suite’s intercepting proxy lets us view and modify requests/responses conveniently and shows how UI responds to them.
Solution:
Due to time constraints, when a secure software development cycle isn’t practised, it is only possible to do ad hoc testing for security. Since the security requirements are not defined, and the sensitivity of the data is not recorded anywhere, it is tough to conclude a security bug. So, the confidence in security test coverage is low. This could lead to an unpredictable release.
We could easily achieve the basic level of security of an application in a new project if we follow the above solutions. In an ongoing project/product, it is partially feasible to implement the BDD method of agile security testing.
Defining security requirements early would avoid conflicts and confusion in the later phases and minimizes security-related bugs. It improves the accountability of the internal team on the security of the application, thereby resulting in a predictable release with minimum cost, stress, and risk.
Authored by Shamphavi Shanmugasundram @ BISTEC Global
The CIA triad is a high-level checklist to evaluate security procedures. It is a vital model used to assess the risks, threats, and vulnerabilities of the system.
The CIA triad, also known as the AIC triad, is a benchmark model to assess Information Security. It guides security professionals in protecting any asset that is valuable for running a business.
Security testing should start from the requirement phase in the Software development lifecycle, and it should be integrated into every phase in SDLC.
CIA triad is helpful in identifying the information to be protected and in defining security requirements needed for an application.
CIA Triad stands for Confidentiality, Integrity, and Availability.
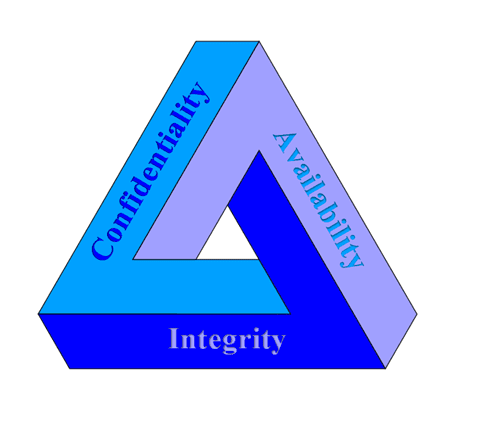
Confidentiality ensures that the system or data is exposed to the right users. This could be ensured by having the following four security measures in an application. They are Identification, Authentication, Authorization, and Encryption.
The confidentiality of an application is assessed by knowing whether the sensitive information in a system is disclosed to unauthorized users. The sensitivity of data is a measure of its importance. The owner of the data decides the sensitivity measure of the data.
Integrity ensures that the data is reliable. The system or data should be accurate, complete, and consistent.
The integrity of the data could be ensured by having proper security measures in our system. Some of them are Hashing, User access controls, Version control, Backup and recovery procedures, Error checking, and Data validation.
The integrity of the data is measured using a factor called the baseline. The baseline is the measure of the current state of the data. The goal of integrity is to preserve the baseline throughout the transaction.
The data or system should be available to the users when and wherever it’s needed. The availability of the application could be ensured by using Hardware maintenance, Software patching/upgrading, Load balancing, and Fault tolerance.
Appropriate levels of availability should be provided based on the criticality of the data. Criticality is the measure of the dependency of a system on data to perform its operation.
CIA triad helps in understanding and prioritizing the severity of a vulnerability in an application. Neglecting the CIA triad makes the application vulnerable to Interruption, Interception, Modification, or Fabrication class of attack.
CIA serves as a yardstick to evaluate the security of an application. If CIA triad standards were met, then the security of that system would be stronger and better equipped to handle threats.
Is CIA Triad enough for Information Security? – No, but it covers most of the security loopholes in an application.
Authored by Shamphavi Shanmugasundram @ BISTEC Global
Building software can be like creating a work of art sometimes. It requires creativity in design, and plenty of craftsmanship to do well. However, over the years, the methods of testing have evolved greatly, and this short blurb focuses on one of the current favorites, the “𝐀𝐠𝐢𝐥𝐞 𝐭𝐞𝐬𝐭𝐢𝐧𝐠” methodology.
As you probably know, Testing is not a phase, but an ongoing activity. all stakeholders including the developers are part of the agile testing method, which results in shortened feedback time. In agile software development in itself driven by testing from the early sprints itself.
“Pair testing” is a notable feature in today’s Agile testing method, where a member of the QA team works closely with a member of the development team to iron out the defects found during each sprint. These informal pairs work together as and when required, speeding up the debugging process effectively. To further strengthen its effectiveness, the team collaborates with the end-user to gather feedback after the completion of each sprint cycle.
Among the key benefits of the “whole-team approach” to product development are the enhanced communication and collaboration within the team, the enabling and best use of the various skillsets that are found within the team for the benefit of the project, and perhaps most importantly, making quality the responsibility of every member of the team.
At the best, Agile development is robust and proactive. Agile testing is robust and energetic the relatively mundane, predictable modules that need testing can easily automated. These include the common regression tests, unit tests, high traffic pages, cross-browser tests, and data-driven tests.
However, it is an important responsibility of the QA team to effectively prioritize the tests that can automated while those such as usability tests, one-off tests, testing the brand new features, and exploratory tests should not automated as they are specific in nature and cannot be reliably carried out by a machine.
These prioritized automated tests, then used by both the development as well as the QA teams. In addition, the QA team enhances the quality of the delivery by implementing performance tests and security tests as they see fit. At times, these tests carried out by specialized members of the QA team.
In the meantime, unit testing generally carried out exclusively by the development team and the responsibility of the entire product does not lie with the developer or the QAE, but with each and every member of the team. Along with their formal expertise, each team member brings in his or her own individual strengths to the table; all of which efficiently used to achieve the common goal of a perfect software product that can implemented at the customer site.
Most importantly, working in collaboration, instead of doing so in rigid isolation, brings about the best in the whole team, in record time. The active participation of a representative from the customer ensures that there are no miscommunications between requirements and products. Good communication among all, from the inception to the completion of the project, ensures that much time and money saved and a great piece of software created.
Authored by Dhara Jayasinghe @ BISTEC Global